Security Maturity: Why You Need It and How to Achieve It

Oliver Presland
Vice President, Global Consulting Services Portfolio
Security risks are everywhere in today’s connected world, impacting individuals and organizations alike. Strengthening security postures is imperative as attacks increase in volume, complexity, and severity. Consequently, organizations must strive to assess and achieve security maturity. This post provides an overview of what security maturity means and five tips to achieve it.
What is security maturity?
The term “security maturity” refers to an organization’s security position relative to its risk environment and tolerances. The risk scenarios will vary greatly according to the organizational environment, as each organization has its own security risk culture. Thus, the level of maturity of the organization is determined by how efficiently it implements security controls, reporting, and processes.
The importance of assessing the security maturity level of an organization. It is impossible to ignore the global increase in security threats, if only in terms of volume and complexity. Business leaders shouldn’t ask if their organization will be attacked, but when and how often. To achieve a high level of prevention, detection, and response, organizations need to shift the mindset to a security-first approach. As security risks affect all parts of an organization, a high level of security maturity is essential to ensure key areas are protected.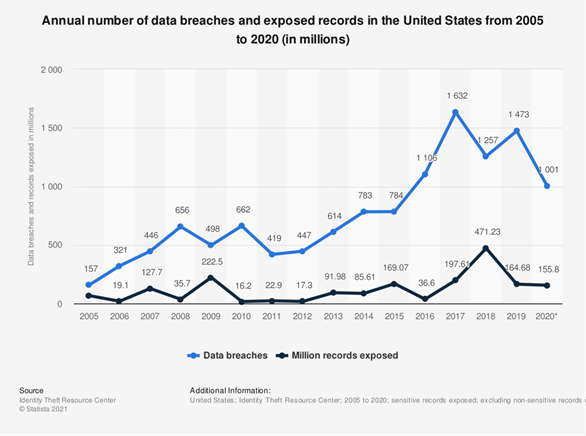 Number of data breaches increasing in the last decade compared with exposed records (Statista)
Number of data breaches increasing in the last decade compared with exposed records (Statista)
The first step to achieve this is to assess the security maturity level. Who may benefit from a security maturity assessment?
Organizations that recognize the need to constantly improve their cybersecurity. Let’s say your organization has a basic level of security controls and policies but has not yet invested in automation or consistent policy management across systems. Before optimizing your security posture, it is important to get an independent review to detect strengths and weaknesses and know which security aspects you should focus on increasing your security maturity.
Organizations undergoing a digital transformation. Before, during and after the transformation, the organization may need to reassess the security level achieved, creating a baseline to ensure the security posture is at least maintained, and preferably enhanced, through the cloud migration.
Regularly audited organizations. Most organizations are the subject of annual audits, often by representatives of external bodies who provide certifications that are key to an organization’s standing in the market. In highly regulated industries this is a key concern. Whether subject to PCI, HIPAA, GDPR, ISO27001 or other audits, conducting a regular assessment of security maturity provides evidence to auditors of the organization’s security stance and security improvements.
Organizations working in hybrid or multi-cloud environments. Each provider has different security controls and policies. Thus, assessing your level of security maturity across these environments helps detect which are providing stronger controls, and enable targeted leveling-up across your integrated environment.
Defining Security Maturity Level
There are five levels of security maturity:
- Information security processes are unstructured and policies undocumented. In this scenario, controls are not automated or reported to the business and are often limited to foundational controls, such as scanning.
- Information security processes are established and policy is informally defined— but only partially applied. In this case, some automation may exist, but with limited business reporting.
- There is more attention to policy documentation, implementation, and automation of controls, with greater levels of reporting.
- The organization controls its information security processes with comprehensive policies, widespread implementation, a high degree of automation, and business reporting.
- The organization has achieved high security maturity. The policy is comprehensive and formally adopted, full deployment and automation of controls have been achieved, and business reporting occurs across all systems. Information security processes are constantly optimized through monitoring. The organization has a cybersecurity-first culture.
Is your organization’s IT security mature enough?
If your internal security monitoring shows that you are not compromised, consider yourself lucky. However, that doesn’t mean you won’t be, or worse, your controls have not yet detected a breach. According to a study by the University of Maryland, there is a new cyberattack every 39 seconds. Therefore, even organizations with the most mature security posture should constantly evolve, reassess, and improve. Optimizing the security maturity of an organization means shifting from a purely reactive security posture to a proactive, security-first approach.
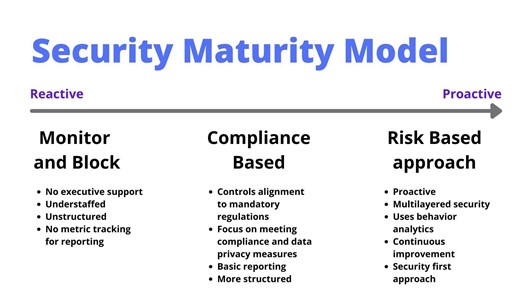
Still, the assessment and actions that work for a large enterprise may not work for a smaller organization. That is why choosing a cybersecurity maturity framework is key. A cybersecurity maturity framework provides a structure in which your organization can assess progress in improving security efforts.
Cybersecurity Maturity Frameworks
There are a number of major cybersecurity frameworks and controls that can commonly be mapped between them, depending on an organization’s preference:
The Center for Internet Security (CIS) Cybersecurity Maturity Model (CMM) is a comprehensive policy, controls, automation, and reporting model that, when followed, provides organizations with confidence that they are managing cybersecurity effectively and protecting themselves from a full spectrum of threats. This framework, originally developed by the U.S. Department of Defense, provides a guide to assess the security maturity of an organization according to its efficiency in meeting a number of controls.
Recently, CIS released version 8, which includes 18 different security controls an organization needs to meet to achieve security maturity. The areas to assess comprise the whole spectrum of security efforts and include control of assets, data protection, access control management, audit log, malware defenses, and more. You can view the complete list here.
National Institute of Standards and Technology (NIST), part of the US Department of Commerce, provides a cybersecurity framework, rather than a model, but it can be used as one. The NIST cybersecurity framework provides five implementation tiers to guide organizations to prevent, detect, and respond to cybersecurity threats.
US Department of Energy’s Cybersecurity Capability Maturity Model (C2M2) is another leading security controls framework that helps organizations measure their information security processes and identify how to improve them on an ongoing basis.
Tips to Reach Maturity Security
When attempting to mature your organization’s security level, we recommend following these steps:
- Create a culture of continuous improvement: Organizations may think that once a high level of security is achieved, there is no need for further efforts. The opposite is true. Since attackers are constantly improving their tactics, organizations need to continuously improve their security measures. Make every effort count by achieving a more secure state with every security iteration. This will create an organizational culture that considers security a continuous activity, constantly reinforcing and strengthening the posture.
- Prioritize security in a security-first approach: These days, almost every organization runs on IT. Thus, cybersecurity should permeate every aspect of the organization and should be a priority for all stakeholders from the CEO to the newest employee. That’s especially true now, when employees often access their corporate networks from home. Implement best practices to ensure security controls are effective and comply with data privacy regulations.
- Automate security controls: Automation is a critical part of achieving a high level of security maturity. Implementing automated solutions provides higher reliability, saves time and effort for security teams, provides better reporting, and allows for a quicker response time. The huge amount of data organizations manage nowadays makes it practically impossible to secure network, infrastructure, applications and data without automated solutions.
- Adopt a cybersecurity model: Choosing a cybersecurity model and sticking to it are more important than which framework you choose. A cybersecurity model will provide a path to follow and a sounding board to refer to. By assessing where you are currently, you will be able to focus on the areas that need strengthening.
- Make cybersecurity a board issue: Cybersecurity should also be an issue for executives and directors. Leaving them in the dark can have disastrous consequences. C-level and senior management can be the prey of social engineering. A recent study revealed that senior executives are nine times more likely to be the target of social breaches. Integrating directors into security discussions, providing business level security and risk management reporting enforces visibility, encourages a proactive stance and enhances the security approach of the organization.
Achieve a High Level of Security Maturity with Ensono
Ensono’s team of expert security associates, including former CISOs, can assess your organization’s security maturity and make actionable recommendations to enhance your controls, processes, and security automation, ensuring compliance.
Ensono is the only MSP that provides end-to-end services from mainframe to cloud. Start your journey to security maturity with the help of our experts’ guidance by requesting a consultation. Let’s talk.
Social Share
Don't miss the latest from Ensono
Keep up with Ensono
Innovation never stops, and we support you at every stage. From infrastructure-as-a-service advances to upcoming webinars, explore our news here.
Blog Post | June 3, 2025 | Industry trends
From Data Center Exit to AI-Ready Cloud: Lessons from the Field
Blog Post | April 16, 2025 | Industry trends
Closing the Cloud Skills Gap with Engineering Talent that Flexes with You
Blog Post | April 8, 2025 | Technology trends